
Europe’s Meteor Missiles Pack The Tech (And Power) To Back Up The Name
techno
Europe's Meteor Missiles: The Game-Changing Tech That's Redefining Air Combat
In the high-stakes world of modern aerial warfare, one missile is quietly rewriting the rules of engagement—and it's not the one you might expect. While the U.S.…

Will Intel’s Core 3 Replicate the N100’s Budget Mini-PC Success?
techno
Intel's Core 3 (Wildcat Lake) Chips: The Next Budget Computing Champion or Just Another Contender?
In the ever-evolving landscape of budget computing, Intel has just dropped a bombshell that's sending ripples through the tech community: the…

CTM360 Report Warns of Global Surge in Fake High-Yield Investment Scams
techno
Global HYIP Scam Surge: 4,200+ Fake Investment Sites Target Millions with "Guaranteed" Returns
A massive wave of fraudulent High-Yield Investment Programs (HYIPs) is sweeping the internet, promising sky-high returns that sound too good to…
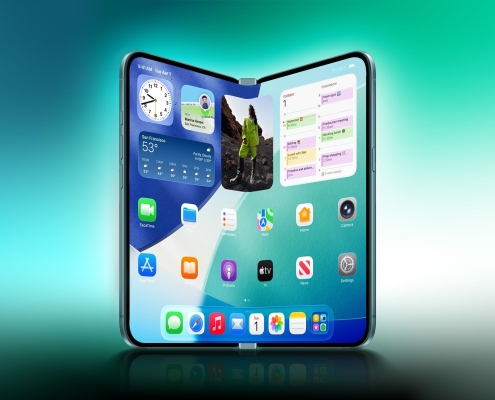
First Foldable iPhone Design Details Revealed
techno
Apple's First Foldable iPhone Design Leaks Reveal Bold New Features and a Radical Redesign
Apple is gearing up to make its grand entrance into the foldable smartphone market, and fresh leaks from a trusted source are painting an exciting picture…

Linux’s Second-in-Command Greg Kroah-Hartman Bestowed With The European Open Source Award
techno
In the ever-evolving world of open-source software, where countless developers dedicate their time and expertise to building tools that power our digital lives, recognition is often scarce. Yet, every now and then, the community comes together…

Securing the Mid-Market Across the Complete Threat Lifecycle
techno
Mid-Market Cybersecurity: The Balancing Act Between Protection and Complexity
In today's hyper-connected digital landscape, mid-market organizations face a cybersecurity paradox: they need enterprise-grade protection but lack enterprise-grade…

Chrome may soon use Gemini antiscam protection to flag scams, but it won’t watch every site you visit
techno
Google Chrome to Get Gemini-Powered Scam Protection Upgrade
In a move that could significantly enhance online security for millions of users, Google is testing a new AI-powered scam protection feature in Chrome that leverages its Gemini technology.…

Loongson 3B6000 Benchmarks: How China’s LoongArch CPU Compares To AMD Zen 5, Intel Arrow Lake & Raspberry Pi 5 Review
techno
Breaking: Loongson 3B6000 LoongArch CPU Faces Off Against AMD Zen 5 and Intel Arrow Lake in First Independent Linux Benchmark Test
In a landmark moment for open-source computing and geopolitical tech independence, the first independent Linux…

ICE and Qatari Security Forces at the Winter Olympics Put Italians on Edge
techno
ICE Controversy Casts Shadow Over 2026 Milano Cortina Winter Olympics
With less than a week remaining before the 2026 Winter Olympics kick off in Italy, the sporting world finds itself embroiled in a security controversy that has nothing to…

Carbon Robotics built an AI model that detects and identifies plants
techno
Carbon Robotics Unleashes AI That Instantly Recognizes Any Plant, Transforming Weed Control Forever
In the quiet fields where farmers have long squinted at the soil, deciding which green shoots are crops and which are invaders, a technological…
