Orchid Security Introduces Continuous Identity Observability for Enterprise Applications
Orchid Security Unveils Identity Dark Matter Discovery Platform to Illuminate Hidden Identity Risks in Enterprise Applications
A New Frontier in Identity Security: From Blind Spots to Complete Visibility
In an era where identity has become the new perimeter, security teams face an increasingly complex challenge: traditional Identity and Access Management (IAM) tools were designed for a different world—one where users, directories, and centralized authentication ruled the landscape. Today’s enterprises run on a sprawling ecosystem of applications, APIs, service accounts, and custom authentication layers, creating vast expanses of “Identity Dark Matter” that exist beyond the reach of conventional security controls.
According to Orchid Security’s latest announcement, this invisible layer of identity usage represents one of the most significant security blind spots facing modern organizations. The company has launched what it describes as the first continuous identity observability platform specifically designed to discover, analyze, and govern identity usage across applications—regardless of whether those identities fall within traditional IAM boundaries.
The Problem: Identity Has Escaped the Stack
The fundamental issue, as Orchid explains, is that identity logic has migrated from centralized directories into application code itself. Credentials are embedded in microservices. Authorization decisions are made locally within applications. Service accounts proliferate without oversight. These identity paths operate outside the visibility of IAM, Privileged Access Management (PAM), and Identity Governance and Administration (IGA) tools.
This creates a dangerous paradox: security teams cannot secure what they cannot see. During audits or incident response, organizations find themselves reconstructing identity behavior from incomplete data, leading to delayed responses and increased risk exposure.
Why Traditional Approaches Are Failing
Most identity security tools rely on configuration data and policy models that work well for managed users but fall catastrophically short when dealing with:
- Custom-built applications with unique authentication logic
- Legacy systems that predate modern IAM standards
- Embedded credentials and secrets scattered across codebases
- Non-human identities like service accounts and API keys
- Access paths that bypass identity providers entirely
The result is a reactive security posture where teams scramble to understand identity risks only after incidents occur or during periodic audits.
Orchid’s Four-Stage Solution: Discover, Analyze, Orchestrate, Audit
Orchid Security addresses this challenge with a comprehensive platform that follows the natural workflow of security teams. The approach begins with lightweight instrumentation that analyzes applications directly to identify authentication methods, authorization logic, and credential usage—both in managed and unmanaged environments.
Discovery: Mapping the Identity Landscape
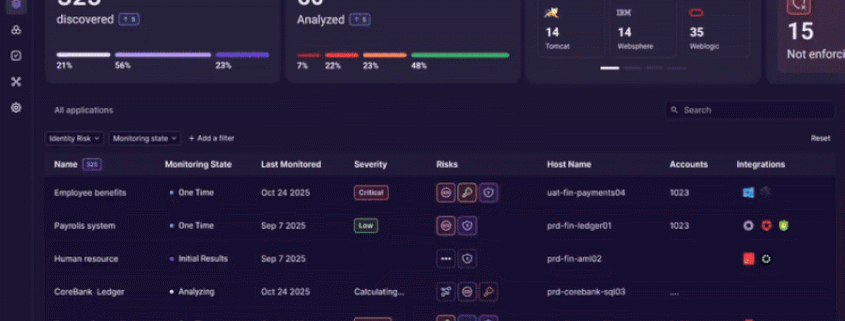
The discovery phase establishes a baseline by creating an accurate inventory of applications and services, identifying all identity types in use, mapping authentication flows, and locating embedded credentials. This isn’t just about finding what’s visible—it’s about illuminating the dark corners where identity risks hide.
Analysis: Risk Assessment Based on Observed Behavior
Once discovery is complete, Orchid analyzes identity usage in context, correlating identities, applications, and access paths to surface risk indicators. The platform identifies shared or hardcoded credentials, orphaned service accounts, privileged access paths outside IAM, and drift between intended and actual access. Critically, this analysis is driven by observed behavior rather than assumed policy, allowing teams to focus on identity risks that are actively in use rather than theoretical vulnerabilities.
Orchestration: Taking Action on Identity Findings
With analysis complete, Orchid enables teams to take coordinated action. The platform integrates with existing IAM, PAM, and security workflows to support remediation efforts. Security teams can prioritize identity risks by impact, route findings to appropriate control owners, and track remediation progress over time. Orchid doesn’t replace existing controls—it coordinates them using accurate identity context.
Audit: Continuous Evidence for Compliance
Because discovery and analysis run continuously, audit data is always available. Security and GRC teams can access current application inventories, evidence of identity usage, and documentation of control gaps and remediation actions. This transforms audit from a periodic scramble into an ongoing process, reducing reliance on manual evidence collection and point-in-time reviews.
Real-World Impact: What Organizations Gain
Organizations implementing Orchid report significant improvements across multiple dimensions: enhanced visibility into application-level identity usage, reduced exposure from unmanaged access paths, faster audit preparation, and clear accountability for identity risk. Most importantly, teams can make decisions based on verified data rather than assumptions.
The Future of Identity Security
As identity continues to move beyond centralized directories, security teams need new ways to understand and govern access. Orchid Security’s approach represents a fundamental shift from reactive identity management to proactive identity observability. By illuminating Identity Dark Matter, organizations can finally see the complete picture of how identity operates across their enterprise—and take control of risks that were previously invisible.
For security leaders grappling with the complexity of modern identity landscapes, Orchid offers a path forward: continuous discovery, contextual analysis, coordinated action, and ongoing audit readiness. In a world where identity is the new battleground, seeing everything is no longer optional—it’s essential.
Tags: #IdentitySecurity #CyberSecurity #IAM #IdentityGovernance #ApplicationSecurity #ZeroTrust #RiskManagement #Compliance #Audit #SecurityOperations #IdentityDarkMatter #OrchidSecurity #EnterpriseSecurity #CloudSecurity #DevSecOps
Viral Phrases: “Identity Dark Matter,” “The new perimeter is identity,” “You can’t secure what you can’t see,” “Continuous identity observability,” “Beyond traditional IAM controls,” “Illuminating hidden identity risks,” “The blind spot in modern security,” “From reactive to proactive identity management,” “Mapping the invisible identity landscape,” “Transforming audit from scramble to strategy”
,



Leave a Reply
Want to join the discussion?Feel free to contribute!