3mdeb Talks Up AMD openSIL & Open-Source Firmware Efforts For Confidential Compute
AMD’s Open-Source Firmware Revolution: Paving the Way for Transparent Confidential Computing
In a groundbreaking development that’s sending shockwaves through the tech industry, AMD is making significant strides toward fully open-source firmware, potentially disrupting Intel’s longstanding dominance in the processor market. At the recent FOSDEM conference in Brussels, engineers Michał Żygowski and Piotr Król from open-source firmware consulting firm 3mdeb unveiled AMD’s ambitious plans to transform the landscape of confidential computing infrastructure.
The OpenSIL Initiative: AMD’s Answer to Transparency
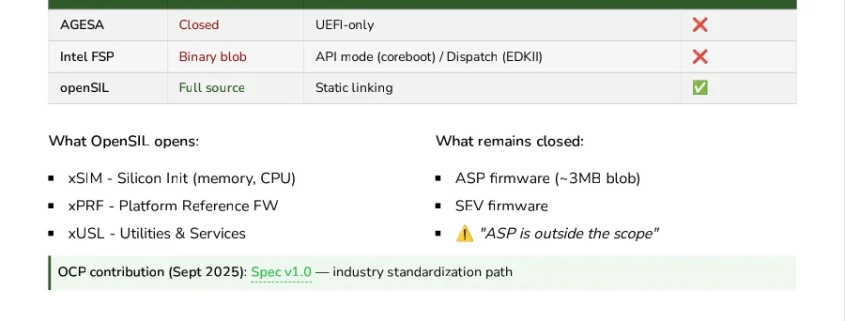
For years, Intel has faced criticism for keeping their Firmware Support Package (FSP) closed-source, limiting transparency and security verification capabilities for enterprise users and security researchers alike. AMD is now positioning itself as the champion of open-source firmware with its OpenSIL initiative, a comprehensive effort to replace the traditional AMD Generic Encapsulated Software Architecture (AGESA) with fully open-source silicon initialization code.
The OpenSIL project represents more than just a technical upgrade—it’s a philosophical shift toward transparency in hardware-software interaction. While production-ready OpenSIL isn’t expected until the Zen 6 architecture release timeframe, AMD has already developed proof-of-concept implementations for both Zen 4 and Zen 5 platforms, demonstrating their commitment to this vision.
3mdeb’s Pioneering Work with EPYC Turin
The real-world implementation of these concepts is being driven by 3mdeb’s work on the GIGABYTE MZ33-AR1 AMD EPYC 9005 “Turin” motherboard. Unlike AMD’s traditional approach of developing OpenSIL on reference motherboard designs, 3mdeb has successfully adapted this retail motherboard to boot with Coreboot and OpenSIL, marking a significant milestone in open-source firmware development.
This achievement is particularly noteworthy because it demonstrates that open-source firmware isn’t just theoretical—it’s practical and deployable on commercially available hardware. The GIGABYTE MZ33-AR1 has become a showcase platform, proving that enterprise-grade computing can embrace open-source principles without sacrificing performance or reliability.
Beyond Basic Functionality: Secure Encrypted Virtualization
3mdeb isn’t stopping at basic boot functionality. Their work extends to supporting SEV-SNP (Secure Encrypted Virtualization – Secure Nested Paging), AMD’s advanced security feature that provides hardware-enforced isolation for virtual machines. By achieving SEV-SNP guest booting with open-source firmware, 3mdeb is addressing one of the most critical needs in modern data centers: confidential computing.
This capability is essential for organizations handling sensitive data, including cloud service providers, financial institutions, and government agencies. The ability to verify and audit the entire firmware stack from silicon initialization through virtual machine launch represents a quantum leap in security transparency.
Timeline and Future Developments
The roadmap for this open-source firmware initiative is aggressive and well-defined. In the first half of 2026, 3mdeb plans to upstream Coreboot support for the GIGABYTE board to the mainline repository, making this functionality available to the broader community. They’re also working on SEV-TIO (Total Memory Encryption with Integrity) support, a new feature in the EPYC Turin processors that provides enhanced memory protection.
Additionally, OpenBMC bring-up for the board is underway, which will provide open-source management controller firmware—a crucial component for enterprise server management and monitoring. These developments collectively create a comprehensive open-source ecosystem for AMD-based servers.
The Broader Impact on Confidential Computing
AMD’s open-source firmware initiative arrives at a critical juncture in computing history. As organizations increasingly move workloads to cloud environments and grapple with data sovereignty requirements, the ability to verify and trust the underlying infrastructure becomes paramount. Open-source firmware provides the transparency needed to audit security implementations, identify vulnerabilities, and ensure compliance with regulatory requirements.
The confidential computing market is projected to grow exponentially as more organizations recognize the importance of hardware-enforced data protection. AMD’s approach could position them as the preferred choice for security-conscious enterprises, potentially reshaping market dynamics in the server processor space.
Technical Deep Dive: How OpenSIL Works
OpenSIL represents a fundamental reimagining of how firmware interacts with silicon. Traditional AGESA code is a complex, proprietary binary blob that handles everything from memory initialization to PCIe configuration. OpenSIL breaks this down into modular, open-source components that can be inspected, modified, and verified by the community.
The architecture allows for greater flexibility in platform support and enables faster identification and resolution of hardware compatibility issues. It also facilitates the development of specialized firmware variants for different use cases, from high-performance computing to embedded systems.
Industry Reactions and Competitive Landscape
The tech industry has responded with cautious optimism to AMD’s open-source firmware push. Security researchers have long advocated for greater transparency in firmware, citing numerous vulnerabilities discovered in proprietary implementations over the years. Hardware vendors and system integrators are particularly interested in the potential for customization and optimization that open-source firmware enables.
Intel, meanwhile, faces increasing pressure to follow AMD’s lead. While the company has made some strides in open-source initiatives, their reluctance to open up FSP remains a significant differentiator. This could influence purchasing decisions for large enterprises and cloud providers who prioritize transparency and security.
Looking Ahead: The Future of Open-Source Hardware
AMD’s OpenSIL initiative is part of a broader trend toward open-source hardware and firmware. As software-defined everything becomes the norm, the importance of transparent, verifiable firmware grows exponentially. This movement extends beyond processors to include network interface cards, storage controllers, and even entire server architectures.
The success of projects like OpenSIL could catalyze similar initiatives across the industry, leading to a future where the entire technology stack—from silicon to software—is open, auditable, and community-driven. This represents a fundamental shift in how we approach computing infrastructure, prioritizing trust and transparency over proprietary advantage.
Conclusion: A New Era of Computing Transparency
AMD’s open-source firmware initiative, as demonstrated by 3mdeb’s work with the EPYC Turin platform, marks the beginning of a new era in computing. By embracing transparency and community collaboration, AMD is not just improving their competitive position—they’re advancing the entire industry toward more secure, trustworthy computing infrastructure.
As we move through 2026 and beyond, the success of these initiatives will likely influence purchasing decisions, shape industry standards, and potentially redefine what enterprise customers expect from their hardware vendors. The era of opaque, proprietary firmware may be drawing to a close, replaced by a future where transparency and security go hand in hand.
Tags and Viral Phrases:
AMD open-source firmware, OpenSIL initiative, confidential computing revolution, EPYC Turin motherboard, Coreboot integration, SEV-SNP secure virtualization, 3mdeb firmware breakthrough, open-source silicon initialization, transparent hardware security, firmware transparency movement, AMD vs Intel firmware war, enterprise confidential computing, hardware-enforced security, open-source server infrastructure, Zen 6 open firmware, firmware vulnerability transparency, secure encrypted virtualization, open-source BIOS replacement, AMD firmware roadmap 2026, enterprise hardware trust, silicon initialization open-source, confidential infrastructure security, open-source hardware movement, firmware auditability, hardware security transparency, AMD competitive advantage, open-source server management, firmware community collaboration, secure computing future, transparent firmware stack, enterprise security requirements, open-source technology revolution, hardware verification capabilities, confidential data protection, open-source firmware ecosystem, AMD market disruption, enterprise purchasing decisions, secure computing infrastructure, open-source hardware trends, firmware development transparency, hardware security standards, open-source enterprise solutions, confidential computing growth, transparent technology stack, hardware trust and verification, open-source security initiatives, enterprise technology transformation, secure infrastructure future, open-source computing revolution.
,



Leave a Reply
Want to join the discussion?Feel free to contribute!