AISURU/Kimwolf Botnet Launches Record-Setting 31.4 Tbps DDoS Attack
AISURU/Kimwolf Botnet Unleashes Record-Breaking 31.4 Tbps DDoS Attack in 35 Seconds—Here’s What You Need to Know
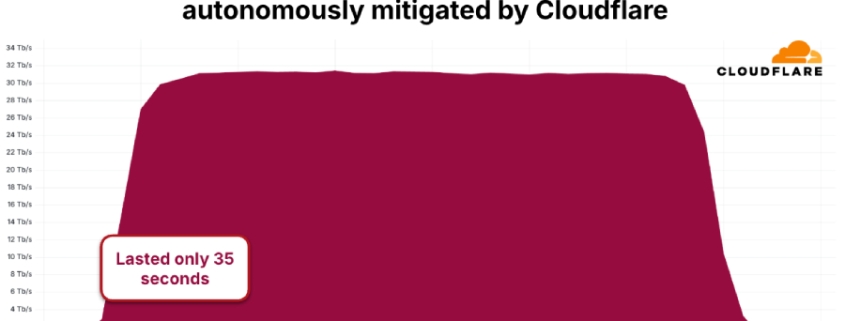
In a stunning display of cyber firepower, the AISURU/Kimwolf botnet has shattered records with a blistering 31.4 Terabits per second (Tbps) DDoS attack that lasted a mere 35 seconds. This hyper-volumetric assault, detected and neutralized by Cloudflare in November 2025, marks a new era of DDoS attacks that are faster, larger, and more destructive than ever before.
The Numbers That Will Make Your Jaw Drop
Let’s talk numbers. In 2025 alone, DDoS attacks surged by a mind-blowing 121%, with Cloudflare automatically mitigating an average of 5,376 attacks every single hour. That’s over 47.1 million DDoS attacks in a single year—more than double the total from 2024. And it’s not just the quantity that’s alarming; the size and sophistication of these attacks are reaching unprecedented levels.
The AISURU/Kimwolf botnet, which has infected over 2 million Android devices, is at the heart of this chaos. Most of these devices are compromised, off-brand Android TVs, often funneled through residential proxy networks like IPIDEA. In fact, Google recently disrupted IPIDEA’s operations, filing lawsuits to take down domains used to control these infected devices.
The Night Before Christmas Campaign
But the record-breaking attack is just the tip of the iceberg. AISURU/Kimwolf was also behind a massive DDoS campaign dubbed The Night Before Christmas, which kicked off on December 19, 2025. During this campaign, the botnet unleashed attacks averaging 3 billion packets per second (Bpps), 4 Tbps, and 54 million requests per second (Mrps). The peak rates? A staggering 9 Bpps, 24 Tbps, and 205 Mrps.
How Did This Happen?
The botnet’s operators have been incredibly resourceful. They’ve used at least 600 trojanized Android apps embedding proxy software development kits (SDKs) to ensnare devices. On top of that, over 3,000 trojanized Windows binaries posing as OneDriveSync or Windows updates have been used to compromise PCs. And let’s not forget the VPN and proxy apps that silently turned users’ Android devices into proxy exit nodes without their knowledge or consent.
Behind the scenes, all these operations are connected to a centralized infrastructure controlled by IPIDEA, a Beijing-based company that has been running at least a dozen residential proxy businesses masquerading as legitimate services.
The Global Impact
The rise of AISURU/Kimwolf has had a global impact. In Q4 2025, hyper-volumetric attacks increased by 40%, jumping from 1,304 to 1,824 attacks. The average size of these attacks grew by over 700% compared to late 2024.
Telecommunications, service providers, and carriers emerged as the most attacked sectors, followed by information technology, gambling, gaming, and computer software verticals. The most attacked countries included China, Hong Kong, Germany, Brazil, the U.S., the U.K., Vietnam, Azerbaijan, India, and Singapore. Meanwhile, Bangladesh surpassed Indonesia to become the largest source of DDoS attacks, with Ecuador, Indonesia, Argentina, Hong Kong, Ukraine, Vietnam, Taiwan, Singapore, and Peru rounding out the top sources.
What’s Next?
Cloudflare warns that DDoS attacks are rapidly growing in sophistication and size, surpassing what was previously imaginable. This evolving threat landscape presents a significant challenge for organizations, especially those relying on on-premise mitigation appliances or on-demand scrubbing centers. It’s time to re-evaluate defense strategies before it’s too late.
As the AISURU/Kimwolf botnet continues to evolve, one thing is clear: the era of hyper-volumetric DDoS attacks is here, and it’s only getting started. Buckle up, because the next record-breaking attack could be just around the corner.
Tags: AISURU/Kimwolf, DDoS attack, 31.4 Tbps, botnet, Cloudflare, IPIDEA, Android TV, cybersecurity, hyper-volumetric attack, The Night Before Christmas, Google, network security, record-breaking attack, cyber threat, malware, trojanized apps, proxy network, DDoS mitigation, telecommunications, global attack, botnet operation, cyber warfare.
Viral Sentences:
- “AISURU/Kimwolf just shattered the DDoS record with a 31.4 Tbps attack in 35 seconds!”
- “2 million Android devices turned into cyber weapons—this is the new face of DDoS attacks.”
- “The Night Before Christmas campaign unleashed attacks at 9 Bpps and 24 Tbps—this is next-level cyber warfare.”
- “Google just disrupted IPIDEA, but the botnet’s operators are still out there, building bigger, badder attacks.”
- “DDoS attacks surged by 121% in 2025—are your defenses ready for the next hyper-volumetric assault?”
- “Bangladesh is now the largest source of DDoS attacks—cybercrime knows no borders.”
- “Cloudflare says it’s time to re-evaluate your defense strategy—because the next attack could be even bigger.”
- “This isn’t just a DDoS attack—it’s a wake-up call for the entire cybersecurity industry.”
,



Leave a Reply
Want to join the discussion?Feel free to contribute!