China-Linked DKnife AitM Framework Targets Routers for Traffic Hijacking, Malware Delivery
Chinese Cyber Espionage Group Unleashes DKnife: The Gateway-Monitoring Nightmare Threatening Millions
In a chilling revelation that’s sending shockwaves through the cybersecurity community, researchers have uncovered DKnife, a sophisticated adversary-in-the-middle (AitM) framework operated by China-nexus threat actors since at least 2019. This isn’t just another malware campaign—it’s a comprehensive cyber warfare toolkit that’s been silently compromising routers, edge devices, and personal computers for years.
The Anatomy of a Digital Predator
DKnife represents the evolution of cyber espionage into something far more insidious. This Linux-based framework comprises seven distinct implants working in terrifying harmony to perform deep packet inspection, manipulate internet traffic, and deliver devastating malware payloads. What makes this particularly alarming is the precision targeting—primarily Chinese-speaking users—suggesting state-sponsored operations with specific geopolitical objectives.
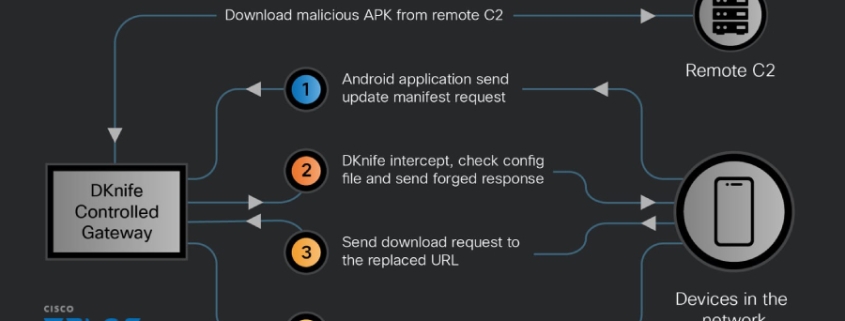
Cisco Talos researcher Ashley Shen pulled back the curtain on this digital menace, revealing how DKnife delivers and interacts with both ShadowPad and DarkNimbus backdoors by hijacking binary downloads and Android application updates. These aren’t amateur operations; we’re talking about tools that have been actively exploiting vulnerabilities and compromising systems across the globe.
A Web of Deception: The Earth Minotaur Connection
The discovery of DKnife came during ongoing monitoring of another Chinese threat activity cluster codenamed Earth Minotaur. This cluster is already linked to sophisticated tools like the MOONSHINE exploit kit and the DarkNimbus backdoor. But here’s where it gets really interesting—DarkNimbus has also been deployed by a third China-aligned advanced persistent threat (APT) group called TheWizards.
The infrastructure analysis uncovered something truly disturbing: an IP address hosting WizardNet, a Windows implant deployed by TheWizards via an AitM framework called Spellbinder. This isn’t just coincidence—it’s a sophisticated ecosystem of interconnected cyber weapons operated by different but aligned threat actors.
Why Chinese Users? The Targeting Strategy
The targeting of Chinese-speaking users isn’t random. Cisco’s analysis revealed configuration files from a single command-and-control (C2) server, suggesting a highly organized operation with potential for broader regional targeting. The evidence is compelling: credential harvesting phishing pages for Chinese email services, exfiltration modules for popular Chinese mobile applications like WeChat, and code references to Chinese media domains.
This targeting strategy makes sense when you consider TheWizards’ known operations across Cambodia, Hong Kong, Mainland China, the Philippines, and the United Arab Emirates. They target individuals and the gambling sector, suggesting economic espionage motives combined with political intelligence gathering.
The Seven-Headed Hydra: DKnife’s Modular Architecture
Unlike WizardNet, which targets Windows systems, DKnife is engineered to run on Linux-based devices—routers, edge devices, and IoT systems that form the backbone of internet infrastructure. Its modular architecture is particularly concerning because it allows operators to serve a wide range of functions, from passive monitoring to active attack.
Let’s break down these seven components that make DKnife such a formidable threat:
1. dknife.bin – The Central Nervous System
This is the brain of the operation, responsible for deep packet inspection, user activity reporting, binary download hijacking, and DNS hijacking. It’s the component that decides what traffic to monitor and how to manipulate it.
2. postapi.bin – The Data Reporter
Think of this as the communication officer, receiving traffic from DKnife and reporting everything back to remote C2 servers. It’s the bridge between the compromised device and the attackers’ command center.
3. sslmm.bin – The Reverse Proxy
Modified from HAProxy, this component performs TLS termination, email decryption, and URL rerouting. It’s particularly dangerous because it can decrypt encrypted communications, exposing sensitive data that users believe is secure.
4. mmdown.bin – The Updater
This module connects to hard-coded C2 servers to download APKs used for attacks. It’s the component that keeps the malware arsenal fresh and evolving.
5. yitiji.bin – The Packet Forwarder
This creates a bridged TAP interface on the router to host and route attacker-injected LAN traffic. It’s like installing a secret backdoor into your local network.
6. remote.bin – The P2P VPN Client
This creates a communication channel to remote C2 servers, establishing a peer-to-peer VPN that makes detection and blocking extremely difficult.
7. dkupdate.bin – The Watchdog
This updater and watchdog module keeps all the various components alive, ensuring the framework remains persistent even if individual components are detected and removed.
The Credential Harvesting Machine
One of DKnife’s most concerning capabilities is its ability to harvest credentials from major Chinese email providers. The sslmm.bin component presents its own TLS certificate to clients, terminates and decrypts POP3/IMAP connections, and inspects the plaintext stream to extract usernames and passwords. These credentials are tagged with “PASSWORD,” forwarded to the postapi.bin component, and ultimately relayed to remote C2 servers.
This isn’t just about stealing email credentials—it’s about gaining access to entire digital lives. With email access, attackers can reset passwords, access financial accounts, and potentially blackmail victims.
Traffic Manipulation at Scale
The core component, dknife.bin, takes care of deep packet inspection, allowing operators to conduct traffic monitoring campaigns ranging from “covert monitoring of user activity to active in-line attacks that replace legitimate downloads with malicious payloads.”
The capabilities are staggering:
- Serving updated C2 to Android and Windows variants of DarkNimbus malware
- Conducting DNS-based hijacking over IPv4 and IPv6 to facilitate malicious redirects
- Hijacking and replacing Android application updates for Chinese apps
- Hijacking Windows and other binary downloads to deliver ShadowPad backdoor
- Interfering with communications from antivirus and PC-management products
- Monitoring user activity in real-time and reporting it back to C2
The Perfect Storm: Why Routers Are the New Battleground
Routers and edge devices remain prime targets in sophisticated targeted attack campaigns. As threat actors intensify their efforts to compromise this infrastructure, understanding the tools and tactics they employ is critical. The discovery of the DKnife framework highlights the advanced capabilities of modern AitM threats, which blend deep-packet inspection, traffic manipulation, and customized malware delivery across a wide range of device types.
This is particularly concerning given recent CISA orders for the removal of unsupported edge devices. The vulnerability of these devices makes them perfect targets for state-sponsored actors looking to establish persistent access to networks and conduct long-term espionage operations.
The Global Implications
What we’re witnessing with DKnife isn’t just another malware campaign—it’s a glimpse into the future of cyber warfare. The sophistication, persistence, and targeted nature of these operations suggest state sponsorship and strategic objectives that go far beyond simple financial gain.
The interconnected nature of the threat ecosystem, with tools like DKnife, WizardNet, ShadowPad, and DarkNimbus being used by different but aligned groups, suggests a coordinated effort to establish cyber dominance. This raises serious questions about international cybersecurity norms and the need for stronger defensive measures.
The Bottom Line
DKnife represents everything that’s terrifying about modern cyber threats: sophistication, persistence, state sponsorship, and the ability to compromise the very infrastructure that keeps the internet running. As routers and edge devices become increasingly targeted, the need for robust security measures and international cooperation has never been more urgent.
This isn’t just a technical problem—it’s a geopolitical one. The discovery of DKnife should serve as a wake-up call to governments, businesses, and individuals alike. In the digital age, our routers aren’t just internet gateways; they’re potential entry points for sophisticated cyber espionage operations that could compromise national security, economic stability, and personal privacy.
Tags: #DKnife #CyberEspionage #ChinaNexus #AitM #ShadowPad #DarkNimbus #RouterSecurity #IoTThreats #CyberWarfare #StateSponsoredHacking #CiscoTalos #EarthMinotaur #TheWizards #Spellbinder #MOONSHINE #LinuxMalware #DeepPacketInspection #TrafficManipulation #CredentialHarvesting #DigitalEspionage
Viral Sentences:
- “The gateway-monitoring nightmare that’s been terrorizing networks since 2019”
- “Seven implants working in perfect harmony to hijack your internet traffic”
- “Chinese-speaking users targeted with surgical precision”
- “Routers: The new battleground in cyber warfare”
- “State-sponsored cyber weapons that evolve faster than defenses”
- “The interconnected ecosystem of digital espionage tools”
- “Deep packet inspection that sees everything you do online”
- “TLS termination that decrypts your ‘secure’ communications”
- “The modular architecture that makes detection nearly impossible”
- “From passive monitoring to active attack in seconds”
- “The cybersecurity wake-up call we can’t ignore”
- “When your router becomes the enemy within”
- “The sophisticated toolkit that’s been hiding in plain sight”
- “Cyber warfare has evolved—and we’re all targets”
- “The geopolitical implications of digital espionage at scale”
,



Leave a Reply
Want to join the discussion?Feel free to contribute!