Kimwolf Botnet Swamps Anonymity Network I2P – Krebs on Security
Kimwolf Botnet Unleashes Chaos on I2P Network in Massive Sybil Attack
In a shocking turn of events, the notorious Kimwolf botnet has unleashed chaos on the Invisible Internet Project (I2P), a decentralized, encrypted communications network designed to anonymize and secure online communications. For the past week, I2P users have been grappling with severe disruptions, as the botnet’s massive influx of infected devices overwhelmed the network, rendering it nearly unusable for legitimate users.
Kimwolf, a formidable botnet that emerged in late 2025, has quickly become a scourge on the internet, infecting millions of poorly secured IoT devices such as TV streaming boxes, digital picture frames, and routers. These compromised devices are transformed into relays for malicious traffic and are capable of launching abnormally large distributed denial-of-service (DDoS) attacks, wreaking havoc on unsuspecting targets.
The I2P network, known for its privacy-focused architecture, operates by routing data through multiple encrypted layers across volunteer-operated nodes. This design ensures that both the sender’s and receiver’s locations remain hidden, providing a secure and censorship-resistant environment for private websites, messaging, and data sharing. However, the network’s resilience was put to the test when Kimwolf’s botmasters began exploiting it as a fallback communication channel to evade takedown attempts against the botnet’s control servers.
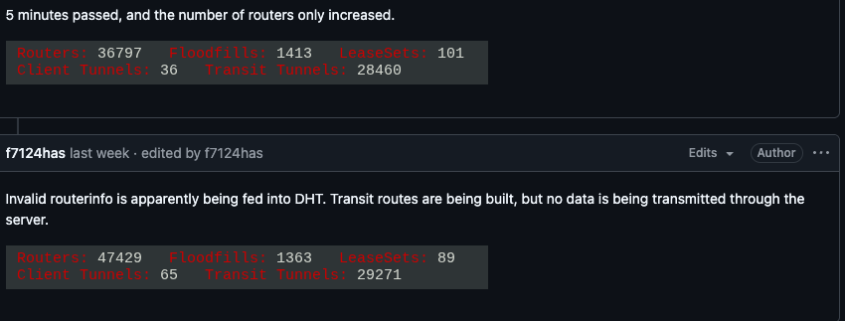
On February 3, I2P users started reporting disruptions on the organization’s GitHub page, describing how tens of thousands of routers suddenly overwhelmed the network. These new routers, unable to transmit data, caused a mass influx that paralyzed the network, preventing existing users from connecting with legitimate nodes. One user reported that their physical router froze when the number of connections exceeded 60,000, highlighting the severity of the attack.
The Kimwolf botnet’s actions constitute a “Sybil attack,” a well-known threat in peer-to-peer networks where a single entity disrupts the system by creating and controlling a large number of fake, pseudonymous identities. The sheer scale of the attack was staggering, with the number of Kimwolf-infected routers attempting to join I2P far exceeding the network’s normal size. I2P’s Wikipedia page states that the network typically consists of around 55,000 computers distributed worldwide, with each participant acting as both a router and a client. However, Lance James, founder of Unit 221B and the original founder of I2P, revealed that the network now comprises only 15,000 to 20,000 devices on any given day.
Benjamin Brundage, founder of Synthient, a startup that tracks proxy services, shed light on the motivations behind Kimwolf’s actions. He explained that the botnet’s operators are experimenting with using I2P and the Tor network as backup command and control channels to maintain stability in the face of ongoing takedown attempts. While there have been no reports of widespread disruptions in the Tor network, the Kimwolf operators’ goal appears to be finding alternative communication methods to keep the botnet operational.
The Kimwolf botnet has previously posed challenges for Cloudflare, as it instructed millions of infected devices to use Cloudflare’s domain name system (DNS) settings. This maneuver caused control domains associated with Kimwolf to repeatedly usurp Amazon, Apple, Google, and Microsoft in Cloudflare’s public ranking of the most frequently requested websites.
Despite the chaos unleashed by Kimwolf, there is a glimmer of hope. Brundage noted that the botnet’s overlords have recently alienated some of their more competent developers and operators, leading to a rookie mistake that caused the botnet’s overall numbers to drop by more than 600,000 infected systems. This development suggests that the botnet’s operators may be losing their grip on the situation, as they continue to test and experiment with their tactics.
As the I2P network struggles to recover from the onslaught, a new release is rolling out, promising stability improvements over the next week for users. Meanwhile, the cybersecurity community remains vigilant, monitoring the evolving threat landscape and working tirelessly to combat the spread of the Kimwolf botnet.
Tags: Kimwolf, I2P, botnet, DDoS, Sybil attack, cybersecurity, IoT, encrypted communications, decentralized network, Tor, Cloudflare, takedown attempts, Lance James, Benjamin Brundage, Synthient, Unit 221B.
Viral Phrases: “Kimwolf botnet unleashes chaos,” “massive Sybil attack,” “overwhelms I2P network,” “millions of infected devices,” “privacy-focused architecture,” “censorship-resistant environment,” “botnet’s numbers drop significantly,” “rookie mistake,” “stability improvements,” “cybersecurity community remains vigilant.”
,


Leave a Reply
Want to join the discussion?Feel free to contribute!