Most Parked Domains Now Serving Malicious Content – Krebs on Security
The Internet’s Parking Lot Has Become a Cybercriminal’s Playground: Direct Navigation Now a High-Risk Activity
In a startling revelation that should send shivers down the spine of every internet user, cybersecurity researchers have uncovered a disturbing truth about what happens when you type a website address directly into your browser. That innocent act of “direct navigation” has transformed from a simple web browsing technique into what experts are calling a “digital minefield.”
A comprehensive new study conducted by Infoblox, a leading cybersecurity firm, has found that the vast majority of parked domains—those placeholder pages that appear when you type in expired website addresses or accidentally misspell popular URLs—have become sophisticated traps designed to redirect unsuspecting users to malicious destinations.
From Safe Harbor to Hostile Territory
The statistics are nothing short of alarming. While a decade ago parked domains redirected users to malicious sites less than five percent of the time, today’s landscape presents a dramatically different picture. According to Infoblox’s extensive research, over 90 percent of parked domain visits now result in users being directed to illegal content, scams, scareware, fraudulent antivirus subscriptions, or outright malware infections.
What makes this particularly insidious is that these redirects happen automatically, without any user interaction. Simply visiting a parked domain from a residential IP address is enough to trigger a cascade of malicious redirects that can compromise your device and personal information.
The Anatomy of a Digital Trap
The mechanism behind these attacks is both sophisticated and troubling. When users attempt to visit expired domain names or accidentally navigate to typosquatting domains—those cleverly crafted misspellings of popular websites—they’re typically brought to placeholder pages managed by domain parking companies. These companies attempt to monetize the misdirected traffic by displaying links to third-party websites that have paid for visibility.
However, what Infoblox discovered is that this monetization model has been hijacked by cybercriminals who have turned these parking pages into sophisticated redirection engines. The process involves multiple layers of profiling and redirection, with each step designed to maximize the chances of delivering malicious content to the victim.
Residential IP Addresses: The New Target
One of the most concerning findings from the Infoblox study is the discriminatory nature of these attacks. Parked websites appear benign when visited using a virtual private network (VPN) or non-residential Internet addresses. However, users accessing these sites from residential IP addresses—the type most commonly used by home internet connections—are immediately subjected to malicious redirects.
For example, customers of Scotiabank who accidentally mistype the domain as “scotaibank[.]com” will see a normal parking page if they’re using a VPN. But if they’re coming from a residential IP address, they’ll be instantly redirected to a site attempting to foist scams, malware, or other unwanted content. This redirect occurs simply by visiting the misspelled domain with a mobile device or desktop computer using a residential IP address.
The Scale of the Operation
The researchers identified a particularly prolific threat actor who owns nearly 3,000 lookalike domains, including “gmai[.]com”—a domain that has been configured with its own mail server for accepting incoming email messages. This means that if you send an email to a Gmail user and accidentally omit the “l” from “gmail.com,” that message doesn’t just disappear or produce a bounce reply. Instead, it goes straight to these scammers.
This domain has also been leveraged in multiple recent business email compromise campaigns, using lures indicating failed payments with trojan malware attached. The threat actor has set up typosquatting domains targeting dozens of top internet destinations, including Craigslist, YouTube, Google, Wikipedia, Netflix, TripAdvisor, Yahoo, eBay, and Microsoft.
A Complex Web of Deception
The redirection process is far from simple. David Brunsdon, a threat researcher at Infoblox, explained that parked pages send visitors through a chain of redirects, all while profiling the visitor’s system using IP geolocation, device fingerprinting, and cookies to determine where to redirect domain visitors.
“It was often a chain of redirects—one or two domains outside the parking company—before threat arrives,” Brunsdon said. “Each time in the handoff the device is profiled again and again, before being passed off to a malicious domain or else a decoy page like Amazon.com or Alibaba.com if they decide it’s not worth targeting.”
This multi-layered approach allows attackers to maximize their chances of success while minimizing their exposure to detection. By profiling the victim at each step, they can tailor their attacks to be more effective and evade security measures.
Government Domains Under Attack
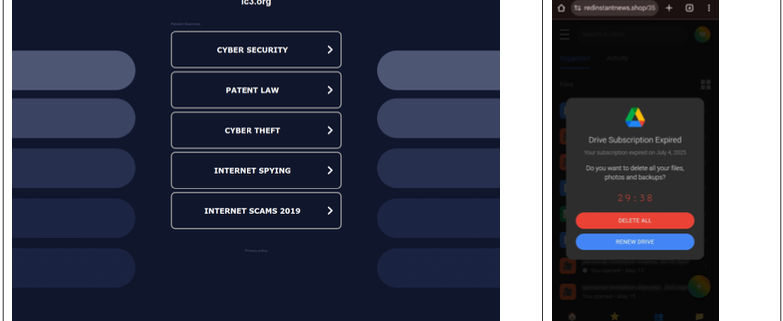
Even variations on well-known government domains are being targeted by malicious ad networks. The researchers discovered that when one of their team members attempted to report a crime to the FBI’s Internet Crime Complaint Center (IC3), they accidentally visited “ic3[.]org” instead of “ic3[.]gov.” Their phone was quickly redirected to a false “Drive Subscription Expired” page.
“They were lucky to receive a scam; based on what we’ve learnt, they could just as easily receive an information stealer or trojan malware,” the report notes. This highlights how even users with good intentions can fall victim to these sophisticated attacks.
The DNS Connection
Infoblox also uncovered a particularly clever exploitation of DNS configurations. A different threat actor who owns “domaincntrol[.]com”—a domain that differs from GoDaddy’s name servers by a single character—has long taken advantage of typos in DNS configurations to drive users to malicious websites.
In recent months, however, Infoblox discovered that the malicious redirect only happens when the query for the misconfigured domain comes from a visitor using Cloudflare’s DNS resolvers (1.1.1.1), and that all other visitors will get a page that refuses to load. This selective targeting demonstrates the sophistication of these attacks and the careful planning that goes into their execution.
Google’s Policy Changes: Unintended Consequences
The Infoblox report also points to recent policy changes by Google that may have inadvertently increased the risk to users from direct search abuse. Google Adsense previously defaulted to allowing their ads to be placed on parked pages, but in early 2025 implemented a default setting that had their customers opt-out by default on presenting ads on parked domains.
This change, while intended to improve ad quality, may have created opportunities for malicious actors to fill the void left by legitimate advertisers. The report suggests that while parking companies claim to only work with top advertisers, the traffic to these domains was frequently sold to affiliate networks, who often resold the traffic to the point where the final advertiser had no business relationship with the parking companies.
The Broader Implications
The transformation of parked domains from relatively safe placeholders to active threat vectors represents a significant shift in the cybersecurity landscape. It demonstrates how cybercriminals are constantly evolving their tactics to exploit new opportunities and how even seemingly innocuous aspects of internet infrastructure can be weaponized.
For everyday internet users, this means that direct navigation—once considered a safe and straightforward way to access websites—now carries substantial risks. The simple act of typing a website address into your browser could potentially expose you to scams, malware, or other cyber threats.
What Can Users Do?
While the situation may seem dire, there are steps that users can take to protect themselves:
- Double-check website addresses before hitting enter, especially for financial or sensitive sites
- Use reputable DNS resolvers and consider using a VPN when browsing
- Be cautious of any unexpected redirects or unusual website behavior
- Keep security software updated and run regular scans
- Report suspicious domains to appropriate authorities
The Road Ahead
As the internet continues to evolve, so too will the tactics employed by cybercriminals. The Infoblox study serves as a stark reminder that cybersecurity is an ongoing battle that requires constant vigilance and adaptation.
For the parking companies, advertising networks, and domain registrars involved in this ecosystem, the findings present both a challenge and an opportunity. By implementing more robust security measures and taking responsibility for the content they facilitate, these organizations can help make the internet safer for everyone.
For users, the message is clear: the internet is no longer the safe playground it once was, and even the most basic online activities now require a heightened awareness of potential threats. As we move forward into an increasingly digital future, staying informed and vigilant will be more important than ever.
Tags and Viral Phrases:
- “Your typo just got you hacked”
- “The internet’s parking lot is now a cybercrime hotspot”
- “90% of parked domains are malicious traps”
- “Direct navigation is dead—long live the redirect”
- “Your innocent typo could cost you everything”
- “Cybercriminals are exploiting your fat fingers”
- “The parking page that wants to rob you blind”
- “When ‘www’ becomes ‘wwworry'”
- “Your keyboard is now a weapon in the hands of hackers”
- “The silent threat hiding in plain sight”
- “From typosquatting to cash grabbing”
- “The parking lot where your data gets jacked”
- “Your browser just became a battlefield”
- “The redirect that could wreck your life”
- “Cybercrime’s newest playground: your address bar”
- “When a simple mistake becomes a security nightmare”
- “The parked domain that’s anything but parked”
- “Your typo is their payday”
- “The internet’s most dangerous dead ends”
- “From innocent mistake to instant infection”
,



Leave a Reply
Want to join the discussion?Feel free to contribute!