If you’ve heard that researchers bypassed Windows Hello on Dell, Lenovo, and Surface laptops, this is everything you need to know.
Lenovo ThinkPad T14s Gen 3
Key Takeaways
- Researchers have managed to bypass Windows Hello on Dell, Lenovo, and Microsoft laptops, highlighting vulnerabilities in the fingerprint scanning technology.
- The fingerprint sensors on these laptops use “Match on Chip” technology to perform biometric verification on their own microprocessors, but this doesn’t inherently prevent spoofing attacks.
- Microsoft’s Secure Device Protection Protocol (SDCP) aims to address these vulnerabilities, but the researchers found that some laptops, including Lenovo ThinkPad T14s and Microsoft Surface Type Cover, didn’t utilize SDCP at all, leaving them more susceptible to attacks.
If you have a Windows laptop, then you probably have come across Windows Hello. It’s a biometric login that on supported laptops, allows users to login with either a facial scan, an iris scan, or a fingerprint scan. In the case of using a fingerprint to get into your laptop, though, be warned: researchers from Blackwing HQ have bypassed Windows Hello on three different laptops from Dell, Lenovo, and Microsoft.
Speaking at Microsoft’s BlueHat conference in Redmond, Washington, Jesse D’Aguanno and Timo Teräs demonstrated how they had managed to bypass Windows Hello on the Dell Inspiron 15, Lenovo ThinkPad T14s, and the Microsoft Surface Pro Type Cover with Fingerprint ID (for Surface Pro 8/X). This meant they were able to gain access to the user account and the user’s data as if they were a normal user. Furthermore, the sensors used on these three devices are from Goodix, Synaptics, and ELAN respectively, meaning that these vulnerabilities aren’t limited to just one fingerprint scanner manufacturer or laptop OEM.
Match on Chip, SDCP, and how laptop manufacturers screwed up

First and foremost, it’s imperative to understand how these fingerprint scanners work and interoperate with the host system. All three fingerprint scanners use “Match on Chip” (MoC) technology, which means they pack their own microprocessor and storage. All fingerprint verification is performed on this chip, including comparing against the database of “fingerprint templates”; the biometric data the fingerprint sensor obtains. This ensures that even if the host machine is compromised (in this case, the laptop itself), the biometric data is not at risk.
Another benefit of MoC is that it prevents an attacker from compromising a spoofed sensor and sending biometric data to the host system. However, it doesn’t prevent a malicious sensor from pretending to be a legitimate one, telling the system that the user has authenticated. It also can’t prevent replay attacks, where an attacker would intercept a valid login attempt and then “replay” it back to the host system. Windows Hello Advanced Sign-in Security (ESS) requires the use of MoC sensors, but you can already see a number of ways that creative attackers may try to get into a user’s laptop. That’s why Microsoft developed SDCP, the Secure Device Protection Protocol.
SDCP has the following goals:
- Ensuring the fingerprint device is trusted
- Ensuring the fingerprint device is healthy
- Protecting input between the fingerprint device and the host
SDCP is a doctrine that states if the system is accepting a biometric login, it can do so with the assumption that the device owner was physically present at the time of login. Functioning on a chain of trust, it aims to answer the following questions about the sensor being used:
- Can the host trust that it’s talking to a genuine device?
- Can the host trust that the device hasn’t been hacked or modified?
- Is the data coming from the device protected?
This is why SDCP creates an end-to-end channel between the host and fingerprint sensor. This leverages Secure Boot, which ensures a model-specific certificate and a private key serve as a chain of trust to verify all communication has been untampered. Compromised firmware can still be used, but the system will know that it has been compromised and modified, and the researchers noted that all devices tested also signed their firmware to prevent tampering.
All of the above sounds good, and SDCP as a concept is a great security feature that OEMs should be using. As a result, it came as a surprise to the researchers when the Lenovo ThinkPad T14s and the Microsoft Surface Type Cover didn’t make use of SDCP at all.
To quote the researchers from Blackwing HQ:
“Microsoft did a good job designing SDCP to provide a secure channel between the host and biometric devices, but unfortunately device manufacturers seem to misunderstand some of the objectives. Additionally, SDCP only covers a very narrow scope of a typical device’s operation, while most devices have a sizable attack surface exposed that is not covered by SDCP at all.
Finally, we found that SDCP wasn’t even enabled on two out of three of the devices we targeted.”
Attacking Dell, Lenovo, and Surface
In the case of the Dell Inspiron 15, the researchers found that they could enroll a fingerprint via Linux, which in turn would not make use of SDCP. While it turns out that the sensor stores two databases of fingerprints for both Linux and Windows (therefore ensuring that SDCP is only used on Windows, and a user can’t enroll on Linux to login on Windows) it’s possible to intercept the connection between sensor and host to tell the sensor to use the Linux database, despite the machine being booted into Windows.
This was all possible thanks to an unauthenticated packet that checked the booted operating system and could be hijacked to point to the Linux database instead. It required using a Raspberry Pi 4 to enroll users into the Linux database and connecting to the sensor manually, but it worked and allowed the researchers to log into the Windows system while using any fingerprint, while still keeping SDCP intact.
Source: Blackwing HQ
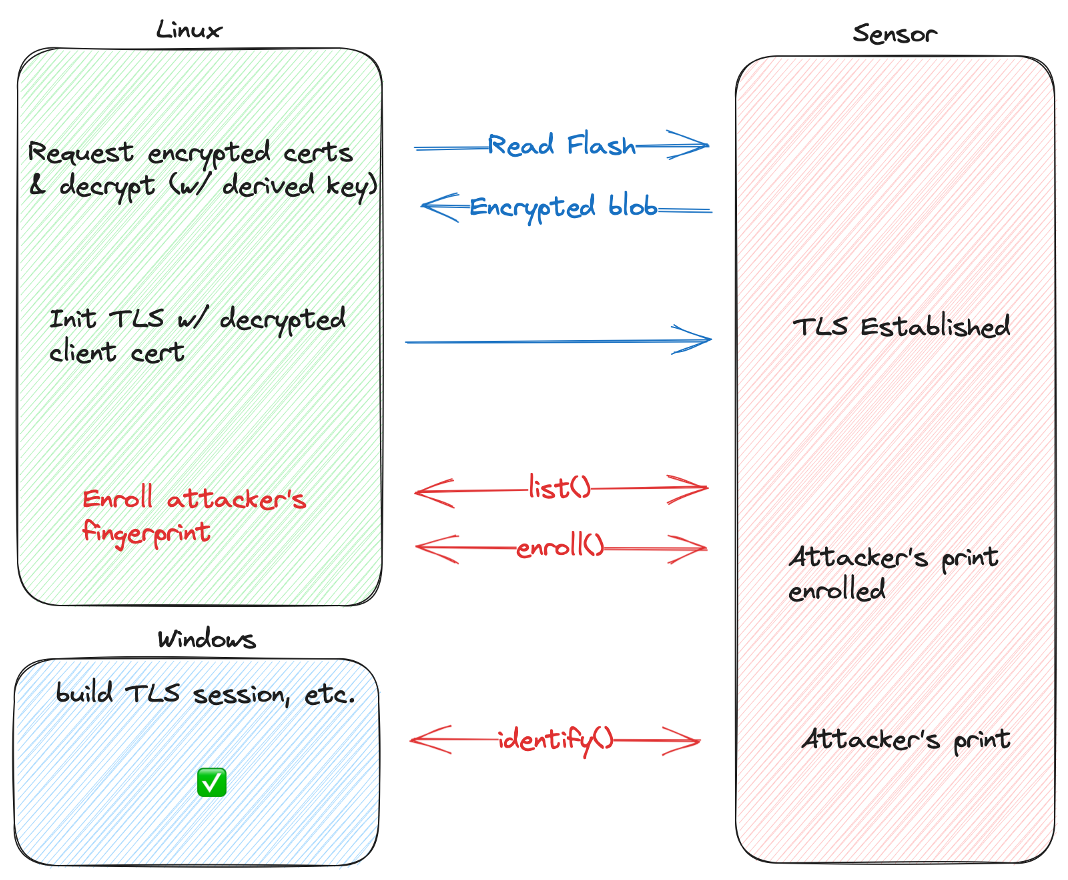
In the case of the Lenovo ThinkPad T14s, it required the reverse engineering of a custom TLS stack securing communication between the host and the sensor, skipping SDCP entirely. The key used to encrypt that communication turned out to be a combination of the machine’s product name and serial number, and exploitation simply because an “engineering problem” as the researchers put it.
Once the attacker’s fingerprint could be forcibly enrolled in the list of valid IDs, it was possible to then boot into Windows and use the attacker’s fingerprint to login to the system.
Source: Blackwing HQ
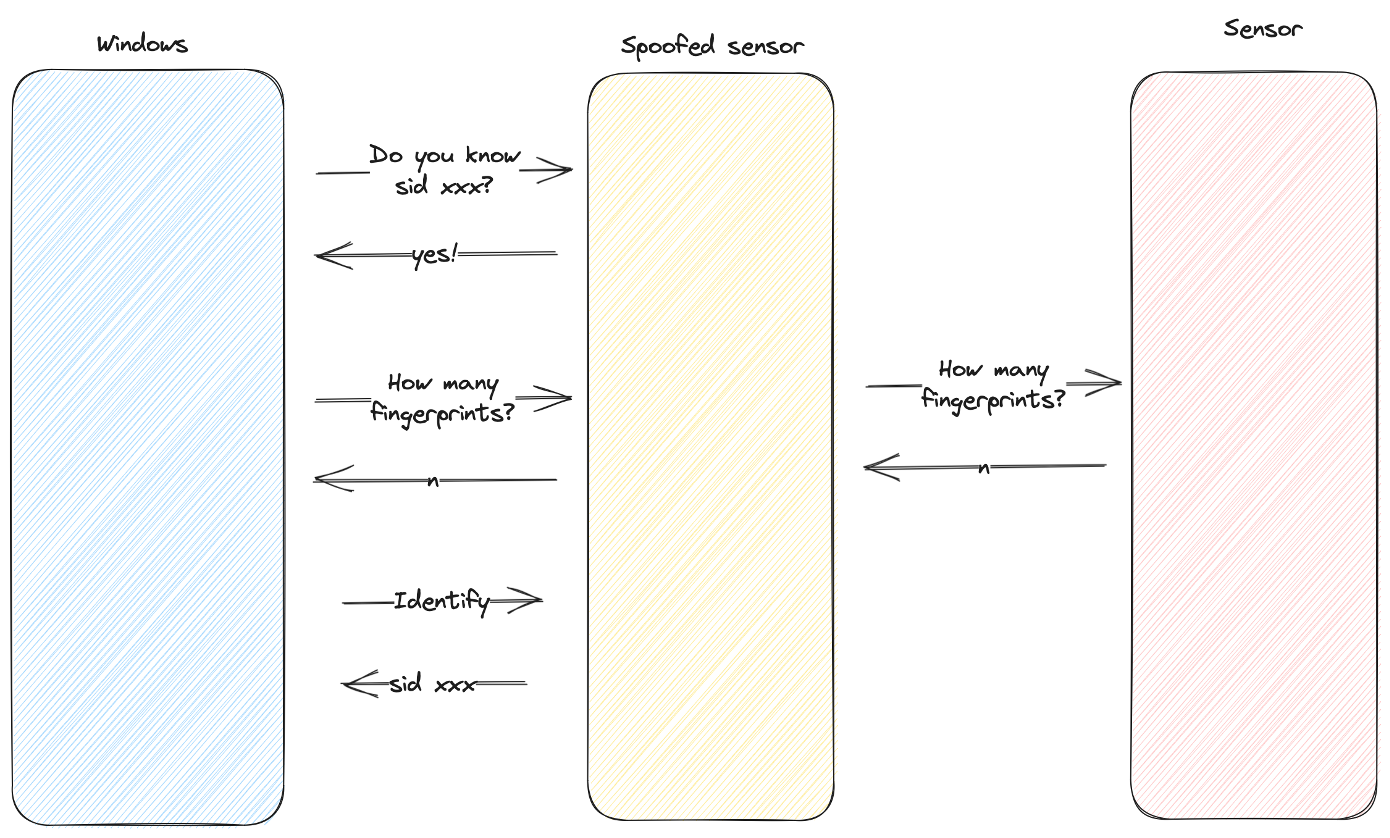
The worst and most egregious of the three comes from the Microsoft Surface Cover’s fingerprint sensor by ELAN. There is no SDCP, it communicates over USB in clear text, and it makes no effort to authenticate the user. The only authentication check it makes is a check with the host system to see if the number of enrolled fingerprints on the host matches the number the sensor has. This can still be easily skirted with a spoofed sensor asking the real sensor how many fingerprints are enrolled.
What can you do?
If you own one of these affected laptops, rest assured that it’s very unlikely any attack like this would happen to you. These are highly-specialized attacks that require a lot of effort on the part of the attacker, and they also need physical access to your laptop. If that is a problem then the best way forward is either to upgrade to a more secure laptop or at least disable Windows Hello entirely.
Disabling Windows Hello should hopefully be enough, as it will require you to login manually and the system won’t be expecting a fingerprint sensor to log in at all. If you still don’t trust your laptop, though, then picking up a new one might be a good idea.



